I got a shiny new device today and the first thing I did was crack it open and heat it to 680 degrees. A good feeling.
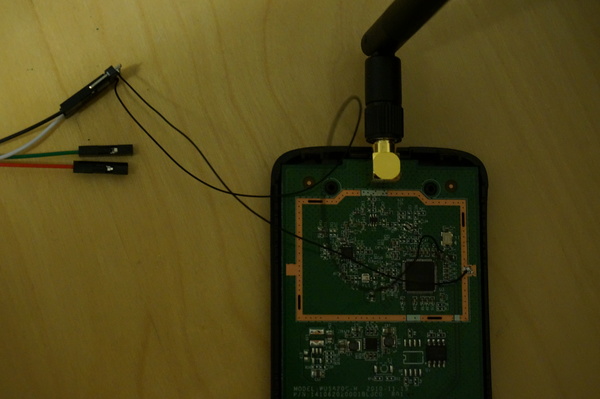
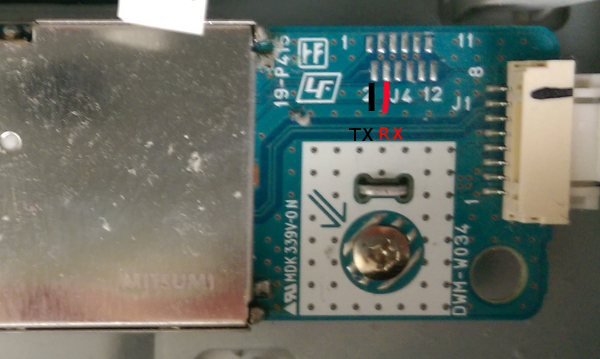
The device in question is an ath9k_htc USB wifi dongle. A colleague suggested this one has an easy to access UART because they brought out the TX/RX pins out from the SoC to dedicated pads. He and I apparently have different definitions for “easy.” Unlike the TP-Link routers which give you through-holes to work with, these are simply SMT pads, and they are tiny in comparison. My soldering iron tip is at least double the size of the pad. Yes, it is somewhat better than trying to solder directly to the pins on the SoC, but not by a whole lot.
As it happens, this is my first attempt at soldering SMT. What could go wrong?
Because the pads are small I used some wire-wrap wire (30 gauge? All I know is that it’s at least two stops smaller than the smallest hole on my wire stripper: getting insulation off was “fun”). During my comedic attempts at getting the wires stuck in the right places, I managed to completely obliterate one of the two pads. Luckily, the one I screwed up was the RX pin, which I don’t really need or care about. Having got the TX and ground wires (badly) soldered in place, I made a some circumspect passes with the magnifying glass and continuity tester to convince myself there were no shorts.
Even so, I am as surprised as you are that it actually worked when I turned it on the first time. And the wifi still works too.
==>[cUSB_REQ_COMP]: 0x%08x
VendorCmd: DownloadComplete!
5. usb only!!
A_WDT_INIT()
==>warm start<==
ALLOCRAM start 0x50d80c size 106484
Enable Tx Stream mode: 0x367
USB mode: 0xf
[+++Magpie_init]
[+++VBUF_init(100)]
[+++VBUF_init(100)]
: Attaching the driver
: Vendor id 0x168c Dev id 0x24
ath_pci_probe 24
ath_hal = 0x00510928
=>[dnQ] 0x0050f288
[ =>[upQ] 0x0050f264
[ =>[hp dnQ] 0x0050f240
[ =>[mp dnQ] 0x0050f21c
[Tgt running]